Security Risk Assessments
Security Evaluation, Strategic Planning, and Technology Architecture
Cyber Security Risk Assessment
In today's cyber landscape, ensuring adequate security is crucial, as it resembles a battlefield. According to CrowdStrike's global threat report from last year, a staggering 80% of cyberattacks utilized identity-based methods to gain access to legitimate credentials. This year, there has been a significant 112% increase in the underground market for access-broker services, indicating that attackers are intensifying their focus on stolen credentials.
To protect critical assets, comply with regulations, and reduce the impact of security breaches, organizations must conduct regular security risk assessments. These assessments are vital for keeping pace with evolving threats and maintaining a robust security posture. By routinely evaluating their security measures, organizations can better anticipate and mitigate potential risks.
Security Risk and Compliance Assessment
A security risk assessment is a systematic process that organizations use to identify, analyze, and prioritize potential security risks and vulnerabilities. By conducting these assessments, businesses can take proactive measures to minimize the financial and reputational impact of data breaches, safeguard sensitive information, and maintain business continuity.
Many industries and regulatory bodies mandate that organizations perform regular security risk assessments to maintain compliance with specific standards, such as GDPR, HIPAA, and PCI-DSS. Failing to meet these standards can lead to substantial fines, operational disruptions, and a loss of trust from stakeholders. Moreover, having a clear understanding of an organization's security posture can provide the confidence needed for strategic decision-making, budget allocation, and effective risk mitigation strategies.
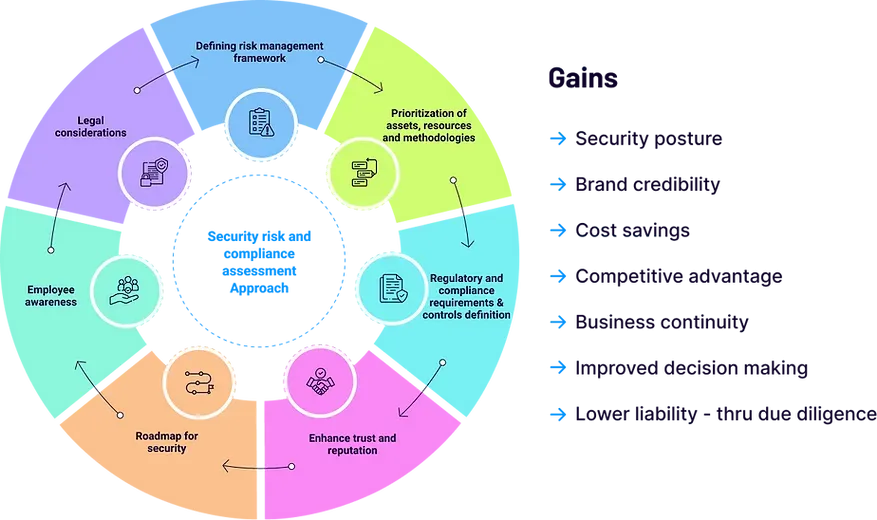
Security Risk and Compliance Assessment Approach
CETC Security Risk Assessment Consultants
Threat and vulnerability assessment
Identify potential threats and vulnerabilities for each asset, considering both external factors (e.g., cybercriminals) and internal factors (e.g., employee behavior).
Risk analysis
The probability and consequences of each identified risk, considering the current security controls and measures in place.
Risk mitigation
Create strategies and outline a roadmap for implementing security controls to mitigate identified risks and reduce their potential impact.
Reporting and communication
Document the assessment process, findings, recommendations, and roadmap to facilitate informed decision-making.
Continuous monitoring and review
Consistently review and update the security risk assessment to reflect changes in the organization's environment, technology, and threat landscape.

